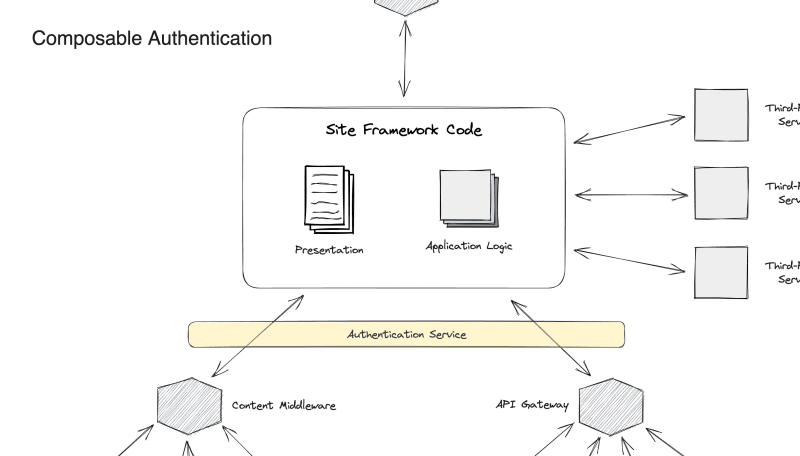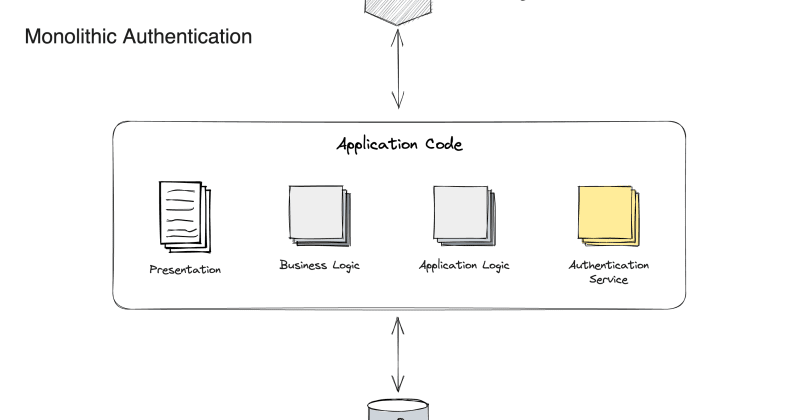
How you approach authentication depends on the rendering method(s) that you’re using.
In monolithic systems, the basics were straightforward. Typically, the server sent a cookie to the browser, which it would receive and could authenticate against for future requests.
Composable systems are often synonymous with heavier client-side interactivity, routing, and access.
As a result, authentication patterns change slightly. The most common pattern is to store session information in a client-side JSON web token (JWT). When a page is rendered requiring authentication, it typically hits an API, providing an encoded version of this token. The API handler decodes and validates the token, then returns the appropriate information if the user is authorized.
Because of the complexity of this pattern and the insecurity of credential-based authentication systems, multiple providers have emerged to provide auth services. Auth0 is a popular choice, but there are many to choose from.
There are also emerging open-source tools, like Auth.js, which are built to integrate an auth solution into specific web frameworks more easily.
In addition, some composable platforms like Netlify also offer an authentication service.