Changelog
-
Google’s Gemini 3.1 Pro Preview model is now available through Netlify’s AI Gateway with zero configuration required.
Use the Google GenAI SDK directly in your Netlify Functions without managing API keys or authentication. The AI Gateway handles everything automatically. Here’s an example using the Gemini 3.1 Pro Preview model:
import { GoogleGenAI } from '@google/genai';export default async () => {const ai = new GoogleGenAI({});const response = await ai.models.generateContent({model: 'gemini-3.1-pro-preview',contents: 'How can AI improve my workflow?'});return Response.json(response);};Gemini 3.1 Pro Preview is available for all Function types. You get automatic access to Netlify’s caching, rate limiting, and authentication infrastructure.
Learn more in the AI Gateway documentation.
-
Anthropic’s Claude Sonnet 4.6 model is now available through Netlify’s AI Gateway and Agent Runners with zero configuration required.
Use the Anthropic SDK directly in your Netlify Functions without managing API keys or authentication. The AI Gateway handles everything automatically. Here’s an example using the Claude Sonnet 4.6 model:
import Anthropic from '@anthropic-ai/sdk';export default async () => {const anthropic = new Anthropic();const response = await anthropic.messages.create({model: 'claude-sonnet-4-6',max_tokens: 4096,messages: [{role: 'user',content: 'How can AI improve my coding?'}]});return Response.json(response);};Claude Sonnet 4.6 is available for all Function types and Agent Runners. You get automatic access to Netlify’s caching, rate limiting, and authentication infrastructure.
Learn more in the AI Gateway documentation and Agent Runners documentation.
-
You can now sync changes from different agent runs in the Netlify dashboard. This is especially helpful if you use Netlify Drop to publish or update your project and don’t use Git workflows to sychronize versions of your project.
Syncing changes helps you and your whole team build and publish faster.
How it works
For example, let’s say you used Netlify Drop to publish your project without setting up a Git workflow.
Next, you decide to use Agent Runners to add a new landing page.
You also start an agent run to update your project’s footer and publish the new footer.
Your agent run for the new landing page doesn’t include the footer changes yet. To get these updates, start a sync run from the Agent Runners dashboard. This will apply all new updates from the live production version of your project.
Now when you publish your landing page updates, you’ll get the updated footer as well.
Syncing changes with Agent Runners enables smoother shipping with several agent runs and with multiple team members working on the same project.
-
Anthropic’s Claude Opus 4.6 model is now available through Netlify’s AI Gateway and Agent Runners with zero configuration required.
Use the Anthropic SDK directly in your Netlify Functions without managing API keys or authentication. The AI Gateway handles everything automatically. Here’s an example using the Claude Opus 4.6 model:
import Anthropic from '@anthropic-ai/sdk';export default async () => {const anthropic = new Anthropic();const response = await anthropic.messages.create({model: 'claude-opus-4-6',max_tokens: 4096,messages: [{role: 'user',content: 'How can AI improve my coding?'}]});return new Response(JSON.stringify(response), {headers: { 'Content-Type': 'application/json' }});};Claude Opus 4.6 is available for all Function types and Agent Runners. You get automatic access to Netlify’s caching, rate limiting, and authentication infrastructure.
Learn more in the AI Gateway documentation and Agent Runners documentation.
-
Here are some Agent Runners improvements that all people with Credit-based pricing plans can enjoy:
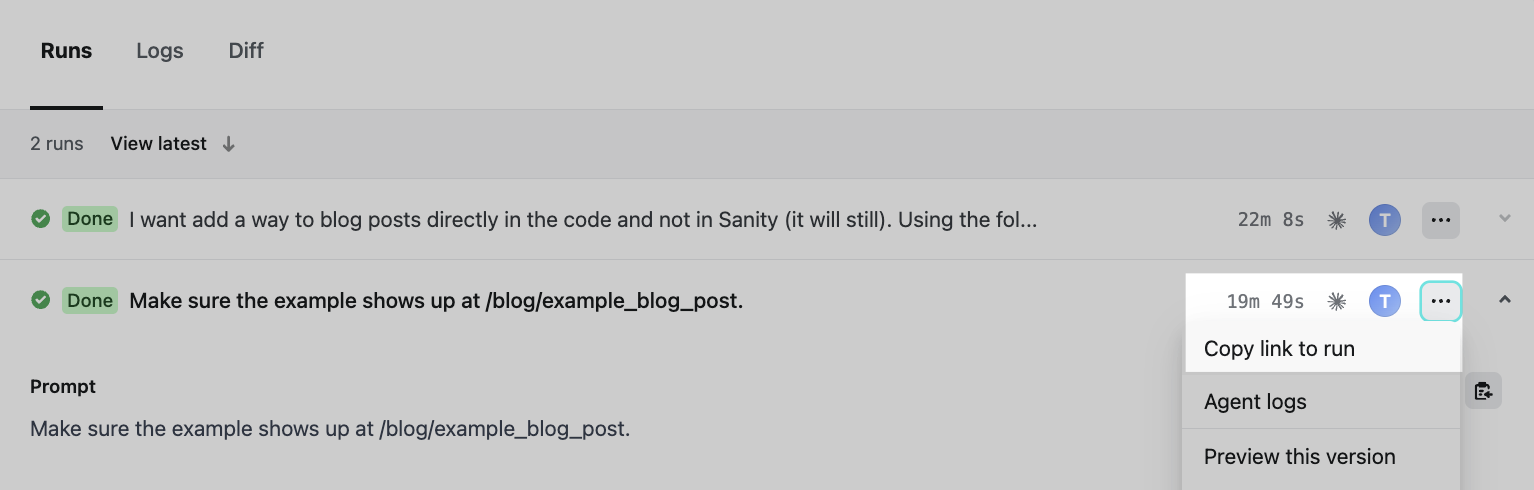
Shareable agent run links
You can now link directly to an agent run to share it with your team or bookmark for later review.
Agent Runners available no matter how you deploy
Agent Runners now supports static projects without build steps. Previously, projects without a build step couldn’t use Agent Runners.
Improved diff view performance
By default, the diff view now loads only the first 50 changed files with an option to load more. This improves performance for large projects.
Feedback welcome
Keep sharing your product feedback about Agent Runners in the feedback form at the bottom of our Agent Runners docs page.
And don’t forget that while you can run multiple agent runs and do other work while they run, you can also play a Netlify game while you wait for the agent to finish.
-
A denial-of-service (DoS) vulnerability (CVE-2026-23864, CVSS 7.5) has been disclosed affecting React Server Components (RSCs), a feature used by Next.js and other React metaframeworks. A malicious payload can cause memory exhaustion or excessive CPU consumption. Next.js has also disclosed two unrelated medium-severity CVEs (CVE-2025-59471, CVE-2025-59472) patched in the same releases. Here’s what Netlify customers need to know.
Impact on Netlify
Nominally, this is a server-side DoS vulnerability. However, on Netlify this has minimal impact: our autoscaling serverless architecture means that a malicious request resulting in a crashed or hung function does not affect other requests. However, active exploitation could increase your function costs.
Affected frameworks
All RSC frameworks are affected:
- Next.js (see version table below)
- React Router 7 (if using RSC preview)
- Waku
@parcel/rsc@vitejs/plugin-rsc
Astro, Gatsby, and Remix are not affected.
React affected versions
See the React blog post for full details.
Affected versions Fixed in 19.0.0–19.0.3 19.0.4 19.1.0–19.1.4 19.1.5 19.2.0–19.2.3 19.2.4 Next.js affected versions
See the Next.js advisory for full details.
Affected versions Fixed in 13.3.0+ EOL - no fix 14.x EOL - no fix 15.0.0–15.0.7 15.0.8 15.1.0–15.1.10 15.1.11 15.2.0–15.2.8 15.2.9 15.3.0–15.3.8 15.3.9 15.4.0–15.4.10 15.4.11 15.5.0–15.5.9 15.5.10 15.x canaries 15.6.0-canary.61 16.0.0–16.0.10 16.0.11 16.1.0–16.1.4 16.1.5 16.x canaries 16.2.0-canary.9 What should I do?
If any of your projects are using an affected version, we recommend upgrading as soon as possible to a patched release.
For Next.js 13.x and 14.x users: patches are not planned for these versions. Consider upgrading to Next.js 15.x or 16.x.
Note that any publicly available deploy previews and branch deploys may remain vulnerable until they are automatically deleted. Consider deleting these deploys manually.
Resources
-
The React Router team has disclosed six security vulnerabilities affecting React Router and Remix. Here’s what Netlify customers need to know.
Vulnerabilities
Vulnerability Remix versions React Router versions & modes CVE-2025-61686 - Path traversal ≤2.17.1 7.0.0–7.9.3
All modesCVE-2025-68470 - Open redirect - 6.0.0–6.30.1, 7.0.0–7.9.5
All modesCVE-2026-22030 - CSRF ≤2.17.2 7.0.0–7.11.0
Framework onlyCVE-2025-59057 - Meta XSS 1.15.0–2.17.0 7.0.0–7.8.2
Framework onlyCVE-2026-22029 - Redirect XSS ≤2.17.3 6.0.0–6.30.2, 7.0.0–7.11.0
Framework, DataCVE-2026-21884 - ScrollRestoration XSS ≤2.17.2 7.0.0–7.11.0
Framework onlyImpact on Netlify
CVE-2025-61686 (path traversal)
This vulnerability affects
@react-router/node,@remix-run/node, and@remix-run/deno. These packages are not used on Netlify, therefore Netlify projects are not affected.CVE-2025-68470 (open redirect)
Apps with unsafe uses of React Router navigation APIs may be hijacked to redirect to arbitrary origins.
Regardless of hosting provider, all apps constructing paths from untrusted user input may be vulnerable.
CVE-2026-22030 (CSRF)
Actions and experimental RSC Server Functions can be triggered by cross-origin form submissions, allowing an attacker to execute actions on behalf of authenticated users.
Regardless of hosting provider, all apps may be vulnerable.
CVE-2025-59057, CVE-2026-22029, and CVE-2026-21884 (XSS)
These are cross-site scripting (XSS) vulnerabilities. For example, in CVE-2026-22029 actions and experimental RSC Server Functions performing a redirect to a path constructed from untrusted user input may be hijacked to execute arbitrary JavaScript in the browser.
Regardless of hosting provider, all apps passing untrusted data into certain APIs may be vulnerable. (The Remix team has left this intentionally vague.)
What should I do?
If any of your projects are using any affected version listed above, we strongly recommend upgrading as soon as possible to patched releases:
react-router7.12.0 or later (for React Router 7.x)react-router6.30.2 or later (for React Router 6.x)@remix-run/react2.17.4 or later@remix-run/server-runtime2.17.4 or later
Note that any publicly available deploy previews and branch deploys may remain vulnerable until they are automatically deleted. Consider deleting these deploys manually.
-
The Node.js team has released a security update addressing a denial-of-service vulnerability affecting applications that use
async_hooks(including in dependencies). Here’s what Netlify customers need to know.Vulnerability
When
async_hooksare enabled on certain versions of Node.js, a stack overflow causes the Node.js process to exit immediately rather than throw a catchable error. This bypassestry-catchblocks and uncaught exception handlers entirely.A malicious actor could send a crafted payload to crash a server.
Note that many common tools and frameworks use
async_hooksunder the hood, notably APM and tracing tools (e.g. DataDog, NewRelic, OpenTelemetry) as well as Next.js App Router and other React Server Components implementations. You can find more details on that here.Impact on Netlify
This is a server-side denial-of-service (DoS) vulnerability. On Netlify, this has minimal impact: our autoscaling serverless architecture means that a malicious request resulting in a crashed or hung function does not affect other requests. However, active exploitation could increase your cold starts and your function costs.
Note that Node.js used during your project’s build is not impacted at all.
What should I do?
If you have opted your Netlify Functions into Node.js 18, we recommend upgrading to Node.js 20 or later. Node.js 18 reached end-of-life in April 2025 and thus will not be patched.
Otherwise, there is no action for you to take. Although this CVE’s impact to Netlify sites is limited, deployed Netlify Functions will be updated to patched Node.js versions automatically on a rolling basis.
For completeness, please note that the Node.js version used during your project’s build is not relevant to this CVE. There is no action for you to take and this will not be automatically patched.
Resources
-
The Svelte team has disclosed five CVEs affecting the Svelte and SvelteKit ecosystem. Here’s what Netlify customers need to know.
Vulnerabilities
- CVE-2026-22775: Memory/CPU exhaustion in
devalue(5.1.0–5.6.1) - CVE-2026-22774: Memory exhaustion in
devalue(5.3.0–5.6.1) - CVE-2026-22803: Server crash in
@sveltejs/kit(2.49.0–2.49.4) - CVE-2025-67647: Server crash and SSRF in
@sveltejs/kit(2.44.0–2.49.4) and@sveltejs/adapter-node(2.19.0–2.49.4) - CVE-2025-15265: XSS in
svelte(5.46.0–5.46.3)
Impact on Netlify
CVE-2026-22775, CVE-2026-22774, and CVE-2026-22803
These are server-side denial-of-service (DoS) vulnerabilities. On Netlify, these have minimal impact: our autoscaling serverless architecture means that a malicious request resulting in a crashed or hung function does not affect other requests. However, active exploitation could increase your function costs.
In addition, note that only sites using the experimental Remote Functions feature are affected.
CVE-2025-67647
As above, this DoS vulnerability involves intentionally “crashing” a server. On Netlify, this has minimal impact.
The SSRF vulnerability affects a
@sveltejs/adapter-node, which is not used by apps deployed to Netlify.CVE-2025-15265
This is a client-side cross-site scripting (XSS) vulnerability. Regardless of hosting provider, all apps using the experimental
hydratablewith unsanitized user-controlled keys are vulnerable.What should I do?
Although the impact to Netlify sites is limited in this case, we always strongly recommend upgrading as soon as possible to patched releases:
devalue5.6.2 or later@sveltejs/kit2.49.5 or later@sveltejs/adapter-node5.5.1 or latersvelte5.46.4 or later
Resources
- CVE-2026-22775: Memory/CPU exhaustion in